COS2626: Assignment 02: Semester 2: October 2015
Question 1
The following questions are based on wireless networking.
1.1 Define the term wireless spectrum.
The wireless spectrum is a continuum of the electromagnetic waves used for data and voice communication.
1.2 Describe the CHARACTERISTICS wireless transmissions have in common with wired transmissions.
Use of the same layer 3 and higher protocols.
Just as with wired signals, wireless signals originate from electrical current traveling along a conductor.
1.3 Describe the DIFFERENCE between wireless and wired transmissions.
The nature of the atmosphere makes wireless transmissions vastly different from wired transmission. Because the air provides no fixed path for signals to follow, signals travel without guidance. This is in contrast to guided media that do provide a fixed signal path.
1.4 Explain why wireless networks are not laid out using the same topologies as wired networks.
Because they are not bound by cabling paths between nodes and connectivity devices, wireless networks, are not laid out the same topologies as wired networks.
1.5 Which WLAN (Wireless Local Area Network) architecture is depicted in the following diagram?
An ad hoc WLAN. In an ad hoc WLAN, wireless nodes or stations, transmit directly to each other via wireless NICS without an intervening connectivity device.
1.6 Explain the ADVANTAGE of having WLANs support the same protocols (for example, TCP/IP) and operating systems (for example, UNIX, Linux, or Windows) as wired LANs.
This compatibility ensures that wireless and wired transimission methods can be integrated on the same network.
1.7 Describe the use of CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) to access a shared medium.
Note the significance of using ACK packets to verify every transmission.
802.11 standards specify the use of CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) to access a shared medium.
Using CSMA/CA, before a station begins to send data on an 802.11 network, it checks for existing wireless transmission. If the source node detects no transmission activity an the network, it waits a brief, random amount of time, and then sends its transmission. If the source does detect activity, it waits a brief period of time before checking the channel again. The destination node receives the transmission and, after verifying its accuracy, issues an acknowledgment (ACK) packet to the source. If the source receives this acknowledgment, it assumes the transmission was properly completed. However, interference or other transmissions on the network could impede this exchange. If, after transmitting a message, the source node fails to receive acknowledgment from the destination node, it assumes its transmission did not arrive properly, and it begins the CSMA/CA process anew.
Question 2
Match each statement with the correct term below. Write only the number of statement and the corresponding term, e.g. 2.1-a
| 2.1 | Displays TCP (Transmission Control Protocol) /IP (Internet Protocol) statistics and details about TCP/IP components and connections on a host. |
| 2.2 | This command provides not only the host’s IP address, but also the primary DNS server name and address that holds the record for this name. |
| 2.3 | Useful only on networks that run Windows-based operating systems and NetBIOS. |
| 2.4 | Both in its simplest form and when used with one or more of its simplest switches, this utility can provide more detailed information than nslookup. |
| 2.5 | The TCP/IP administration utility for use with Windows operating systems. |
| 2.6 | Allows you to view a host’s routing table. |
| 2.7 | Used if an administrator already know a host’s name and wants to learn its IP address. |
| 2.8 | The TCP/IP configuration and management utility used on UNIX and Linux systems. |
| 2.9 | Uses ICMP (Internet Control Message protocol) ECHO requests to trace the path from one networked node to another, identifying all intermediate hops between the two nodes. |
| a. | ipconfig utility |
| b. | ifconfig utility |
| c. | netstat utility |
| d. | nbstat utility |
| e. | host utility |
| f. | dig utility |
| g. | nslookup utility |
| h. | route utility |
| i | traceroute utility |
Solution:
| 2.1 | C |
| 2.2 | g or f |
| 2.3 | d |
| 2.4 | f or g |
| 2.5 | a |
| 2.6 | h |
| 2.7 | e |
| 2.8 | b |
| 2.9 | i |
Question 3
Study the following diagram depicting the elements of virtualization. Identify components ‘A’, ‘B’ and ‘C’ respectively.
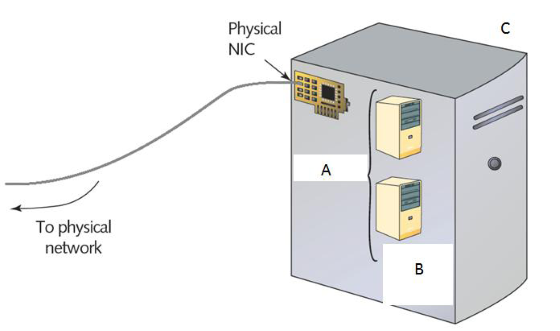
A: Hypervisor
B: Virtual machines (Geusts)
C: Physical computer (host)
Question 4
Study the following diagram depicting a VPN (Virtual Private Network) connection and answer the questions that follow.
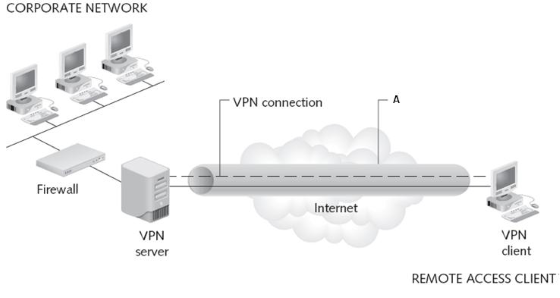
4.1 Define a VPN.
VPNs are wide area networks that are logically defined over public transmission systems.
4.2 What are TWO important considerations when designing a VPN?
Interoperability and security.
4.3 What does the letter ‘A’ in the diagram represent?
Tunnel
Question 5
Name and discuss FIVE factors that cloud computing is distinguished by.
1. Self-service and on demand – Services, applications and storage in a cloud are available to users at anytime, upon the users request.
2. Elastic – The term elastic in cloud computing means that services and storage capacity can be quickly and dynamically – sometimes even automatically – scaled up or down.
3. Support for multiple platforms – Clients of all types, including smartphones, laptops. desktops, thin clients and tablet computers can access services, application and storage in a cloud, no matter what operating system they run or where they are located, as long as they have a network connection.
4. Resources pooling and consolidation – In the cloud, as on host computers that contain multiple virtual machines, resources such as disk space, applications and services are consolidated. That means one cloud computing provider can host hundreds of web sites for hundreds of different customers on just a few servers.
5. Metered services – Whether the cloud provides applications, desktops, storage, or a service, its use is measured. A service provider may limit or charge by the amount of bandwidth, processing power, storage space, or client connections available to customers.
Question 6
The following questions are based on security policies.
6.1 Define a security policy.
A security policy identifies your security goals, risks, levels of authority, designated security coordinator and team members, responsibilities for each team member and responsibilities for each employee.
6.2 Name THREE typical goals for security policies.
Ensure that authorised users have appropriate access to the resources they need.
Prevent unauthorised users from gaining access to the network, systems, programs, or data.
Prevent accidental damage to hardware or software.
6.3 Name FOUR possible subheadings for the policy outline.
Password policy, software installation policy, network access policy, e-mail use policy etc.
6.4 A security policy should define what confidential means to the organization. Define term confidential.
In general, information is confidential if it could be used by other parties to impair an organization’s functioning, decrease customer’s confidence, cause a financial loss, damage an organization’s status or give a significant advantage to a competitor.
Question 7
7.1 Define the term backup
A backup is a copy of data or program files created for archiving or safekeeping.
7.2 Define the term optical media and provide examples.
Optical media is a type of media capable of storing digitised data and that uses a laser to write data to it and read date from it. Examples of optical media include all type of CDs, DVDs amd Blu-Ray discs.
7.3 Name THREE DISADVANTAGES of optical media.
1. Because of their modest storage capacity, recordable DVDs and BLu-ray discs may be an adequate solution for home or small office network, but they are not sufficient for enterprise networks.
2. Another disadvantage to using optical media for backups is that writing data to them takes longer than saving data to some other types media, such as tapes or disk drives, or to another location on the network.
3. In addition, using optical media requires more human intervention than other backup methods.
7.4 Describe how tape backup might be implemented on both small and large networks.
On a relatively small network, stand-alone tape drives might be attached to each server. On a large network, one large, centralized tape backup device might manage all of the subsystems’ backups.
7.5 Describe how to perform network backups if an organization does not have a WAN or a high-end storage solution.
If your organization does not have a WAN or a high-end storage solution, you might consider online backups. An online backup, or cloud backup, saves data across the internet to another company’s storage array. Usually, online backup requires you to install their client software. You also need a (preferably high-speed) connection to the internet.
7.6 Describe the Grandfather-Father-Son backup rotation scheme.
When planning your backup strategy, you can choose from several standard backup rotation schemes. The most popular of these schemes, called Grandfather-Father-Son uses daily (son), weekly (father) and monthly (grandfather) backup sets. Three types of backups are performed each month: daily incremental (every Monday through Thursday), weekly full (every Friday) and monthly full (last day of the month).
